Hello together,
recently I found a pretty nice error 🙂 at the FortiGate SSLVPN Client. I know some of the errors, Connecting Error (40) I didn’t see before.
After I tried to connect, I received at state „Connecting… (40)“ – „Unable to establish the VPN connection. The VPN server may be unreachable. (-5)“ But what happens?
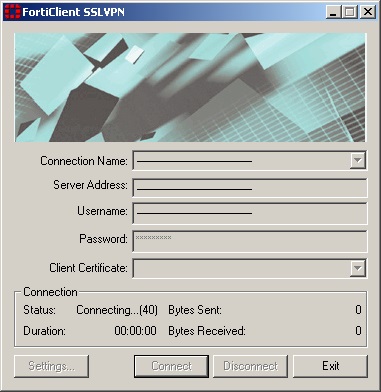
Google presents many of Blog which presents a solution without the understanding behind them why the solution is working ? in this case, it’s a workaround. I tried from MTU change to IPS Service reboot everything but nothing helps. An MTU change sounds to be a workaround of an MTU Path Discovery Issue. The IPS Service could be a FortiGate overload issue, but all of the points don’t describe the real reason, why it’s not functioning. Let’s try to find out, what’s the real problem is.
The first steps i do were :
– Check if the SSLVPN Port is open via telnet 10443 „Connecting… (10)“ – OK
– When the Port is open, the SSLVPN service is reachable, up and running.
What happens at state 40 ?
=> SSL/TLS Certificate Check
Which settings use Fortinet FortiGate SSLVPN Client ?
=> Microsoft Internet Explorer
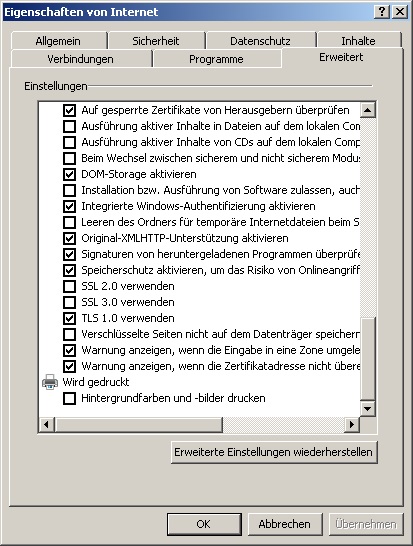
Which settings should be set at Microsoft Internet Explorer ?
=> TLS 1.0
Which Operating System is used ?
=> Microsoft Windows XP
Which SSL/TLS Protocol does Microsoft Windows XP support ?
=> SSLv2 – unsecure (disabled)
=> SSLv3 – unsecure (disabled)
=> TLS1.0 – Problem because maximal TLS 1.0
Which SSL/TLS Protocols does FortiGate Firewall support ?
FortiGate # get vpn ssl settings | grep tls
tlsv1-0 : disable
tlsv1-1 : enable
tlsv1-2 : enable
dtls-tunnel : enableFortiGate # config vpn ssl settings
FortiGate (settings) # set tlsv1-0 enable
FortiGate (settings) # endFortiGate # get vpn ssl settings | grep tls
tlsv1-0 : enable
tlsv1-1 : enable
tlsv1-2 : enable
dtls-tunnel : enableTry to connect…
Tadaaa !!!
It looks like to be a real solution because the real issue is located. In this case, it is possible to use an Operating System which supports TLS 1.1 and 1.2 or to activate TLS 1.0 at the FortiGate Firewall. It’s your choice.
Version 5.4.3 change the ciphers automaticly to high !
Lets debug the SSL VPN service.
FortiGate # diagnose debug application sslvpn -1
FortiGate # diagnose debug enableStart SSL-VPN Connection
[75:root:61]Destroy sconn 0x329ae300, connSize=0. (root)
[75:root:62]allocSSLConn:264 sconn 0x32914300 (0:root)
[75:root:62]SSL state:before/accept initialization (84.16.30.46)
[75:root:62]SSL state:fatal handshake failure (84.16.30.46)
[75:root:62]SSL state:error:(null)(84.16.30.46)
[75:root:62]SSL state:error:(null)(84.16.30.46)
[75:root:62]SSL_accept failed, 1:no shared cipher
[75:root:62]Destroy sconn 0x32914300, connSize=0. (root)
[75:root:63]allocSSLConn:264 sconn 0x329ca300 (0:root)
[75:root:63]SSL state:before/accept initialization (84.16.30.46)
[75:root:63]SSL_accept returned 0.„no shared chipher“, let’s go to change that.
FortiGate # config vpn ssl settings
FortiGate (settings) # set algorithm medium
FortiGate (settings) # endTry again and „Tadaa“, again !!!
Thumbs up, if you could resolve your issue by this article and write something into the commentary 😉 Thanks in advance!







‚Been trying to fix this on my Windows 7 for a week now. Your post is a lifesaver. Thanks!
Worked like a charm, was breaking my head with google for very long until i ended here….
That is the truly fix! Congrats for the real troubleshooting here.
Worked well, thank you 🙂
Awesome, Thanks a lot
Superrrrrrr Thanks a lot.
Can u help me for -455 error in fortigate on windows 10.i have tried with wan miniport repair n install but still issue remains same.
Thanks in advance
Hey Kashif,
post the extact error message! If you fight with the WAN Mini Port, then seems to be a challenge with an IPSec Tool.
Lovely…Worked like a Charm!
Welcome 🙂
with win 7 , i fixed was enable TSL 1.1 and TSl 1.2 in internet option-> tab advanced -> sercurity
Thank you for the tip!
Cool Tuan 🙂
This post is Windows XP related. Of course it could the the other way around.
In FortiOS is TLS 1.1 and TLS 1.2 enabled but not in Windows 7.
Thanks to let us know!
Cheers mate!
Very good article
Thank you!
heyy
Im getting the message same message on debug log „SSL_accept failed, 1:no shared cipher“ but i cant find the attribute for „set algorithm“ in the cli, please help how do i fix that?
Hey Ismailo,
this command should still be supported in version 5.4. Let me know which version is running.
Because i don’t know how familiar your are with FortiOS i start from scratch.
1. config vdom (if you have some)
2. edit „vdomname“
3. config vpn ssl settings
4. set ?
Post the output of the CLI here, please. Or paste the output where you stuck.
Cheers
Hi Isailo,
i got the same that i do not have the option to say set algorithm medium. What would be the next step i could try? V5.6.0
thank you! this post was helpful, currently there is almost similar behavior in Win10 1803, Microsoft’s KB 4458166, released on Tuesday. I use FortOS 6.02 with default tlsv1-0 disable.
heyy
Im getting the message same message on debug log “SSL_accept failed, 1:no shared cipher” but i cant find the attribute for “set algorithm” in the cli, please help how do i fix that?
I have same issue, can you please explain which VDOM to configure SSL.root or the one going out to WAN? can somebody please explain
Thank you so much you save my day ^^
I am very grateful for your efforts put on this article.
This article is very informative, updated and translucent.
Can I expect you may post this type of another article inthe nearr future?
Best regards,
Boswell Valenzuela
i can not run the command: get vpn ssl settings | grep tls
u can see output in the picture